Lockbit, Ransomware as a Service & Outlawing Payments
Written on
This post is adapted from a paper I wrote for a masters course in early 2024.
Introduction
Ransomware is a global problem that has significant financial and business operations impact to organisations that are victims of attacks. The proliferation of Ransomware as a Service (RaaS) has led to an explosion of ransomware attacks by lowering the bar to entry for an individual or group that has interest in conducting a ransomware attack. One of the largest RaaS operators in existence today is the Lockbit ransomware group. Lockbit is both the name of the RaaS operators and the malware that they use to encrypt and exfiltrate data from their customer’s targets.
This posting explores the Lockbit malware and how the RaaS operators function. Beginning with a description of the RaaS business interactions with their affiliates to explain how the ransomware and associated tools are sold and supported.
Following the explanation of the RaaS business operations details of the main Lockbit Windows ransomware, Linux ESXi ransomware and the information stealer dubbed StealBit will be explored. The Tactics Techniques and Procedures (TTPs) of the affiliate threat actors and ransomware will be explained in detail as well as defense and mitigation actions that organisations can take to protect against Lockbit.
I conclude with some details of the costs and impact to Lockbit victims. Financial losses as well as impact to business operations and human life are recounted to convey an understanding of the magnitude of the impact of Lockbit has on victim organisations across the globe. Finally closing out with my thoughts on outlawing ransomware payments.
Lockbit: When Ransomware Becomes a Business
The ransomware now known as Lockbit was first observed in September of 2019 which at the time was dubbed “ABCD” ransomware due to the file extension “.abcd” used in the original version of the virus. The name Lockbit emerged in January of 2020 when it was observed on Russian-language based cybercrime forums. Since its emergence in 2019 the ransomware has steadily evolved into a more functional attack tool with Lockbit 2.0 being released in June 2021, Lockbit Linux-ESXi locker version1.0 emerging in October 2021, Lockbit 3.0 being released in March 2022 and most recently Lockbit Green being released in January 2023 1. After an internationally coordinated effort disrupted Lockbit 2 Lockbit was updated with new encryptors 3 when the Lockbit operators restored their services. Lockbit has been developed over several years and as a result it has gained more advanced attack methods and expanded the number systems it is able to discover, compromise and encrypt. The main Lockbit malware is capable of encrypting windows based devices and files of the victim machines it runs on, Lockbit Linux-ESXi Locker is capable of encrypting the Linux operating system as well as VMware ESXi environments taking down entire VMware virtual machine farms. The data exfiltration tool Stealbit is capable of exfiltrating victim data to custom built dark web sites to avoid law enforcement takedown of commercial sites previously used for dumps of victim data. Lockbit is combined with many other tools to conduct multiple malicious activities in compromised networks “During their intrusions, Lockbit affiliates have been observed using various freeware and open-source tools that are intended for legal use. When repurposed by Lockbit, these tools are then used for a range of malicious cyber activity, such as network reconnaissance, remote access and tunnelling, credential dumping, and file exfiltration.” 4. The combination of an advanced malware with other free and open-source tools makes for an extremely effective arsenal that can be used for lateral movement, widespread compromise of systems and data exfiltration. Attackers using Lockbit aim for maximal compromise of systems to ransom combined with large amounts of data exfiltration to provide incentive for victims to pay to restore their systems, stop public exposure of the attack and resulting data breach. These techniques have proven to be extremely effective and profitable for attackers using Lockbit for extortion.
Lockbit is the name of the malware as well as the title for the threat actors that sell the malware as Ransomware as a Service (RaaS). The LockBIt operators function as a business with a model of selling the malware and required support to affiliates which then use the malware to attack organisations and extort them for financial gain. Affiliates pocket the money extorted through their attacks and pay the Lockbit RaaS group a percentage of the money for use of their malware and other supporting infrastructure. “Lockbit operated as a ransomware-as-a-service group, wherein the ransomware gang takes care of everything from the bulletproof hosting and domains to the development and maintenance of the malware. Meanwhile, affiliates are solely responsible for finding new victims, and can reap 60 to 80 percent of any ransom amount ultimately paid to the group.” 2. The RaaS operators function like a business providing customer support to affiliates to deploy their ransomware, exfiltrate data and extort the target. Lockbit operators tend to be competitive and run advertising campaigns such as paying people to have their logo tattooed on their body and publicly insulting their competition to garner brand recognition and gain new customers.
Figure 1: Screenshot of Lockbit support site
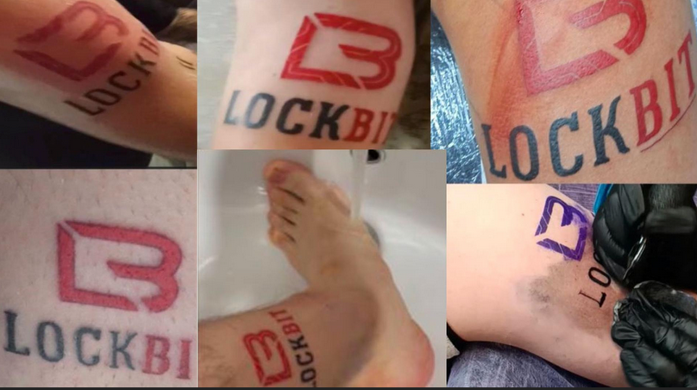
Figure 2 Lockbit promotional tattoos
The combination of an advanced malware with a mature RaaS organisation has made for a highly effective cybercrime enterprise. Lockbit has evolved to become one of the most prevalent and profitable RaaS strains in 2023. Lockbit was able to take advantage of law enforcement disruption of other RaaS providers to gain new customers and increase profits in late 2022.
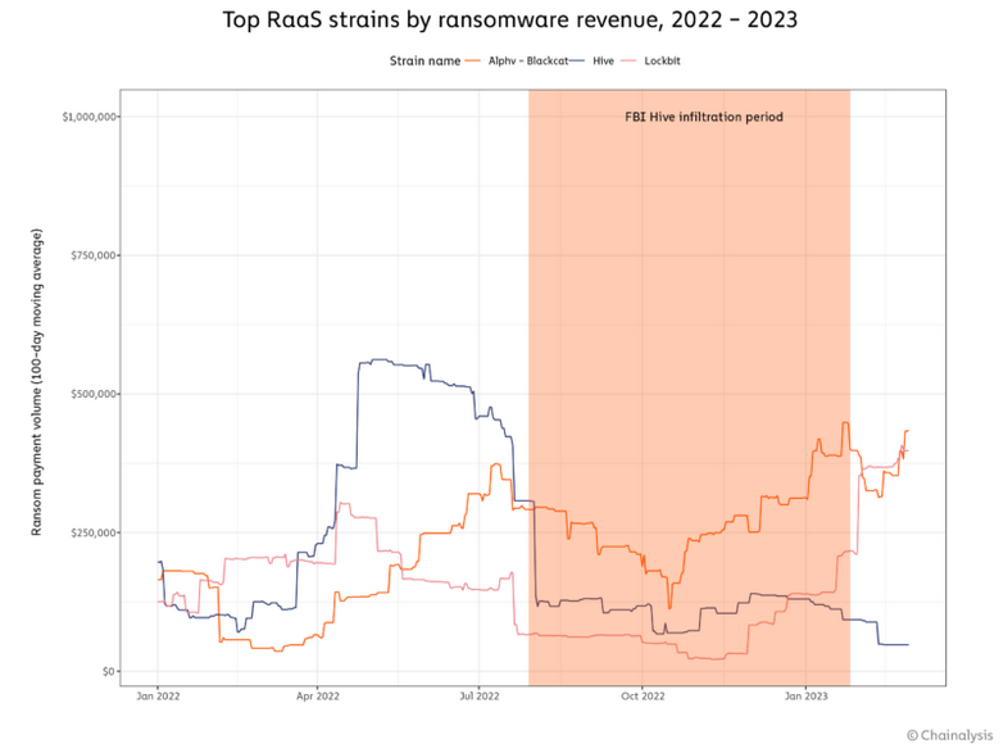
Figure 3: Top RaaS revenue 5
Lockbit Tactics Techniques & Procedures (TTPs)
Since Lockbit is RaaS it is deployed by different affiliates which leads to the tactics, techniques, and procedures (TTPs) being extremely varied and complicated. Different Lockbit affiliates will use different methods for everything from first compromise to lateral movement making defending against the malware that much more difficult as one defending against one set of TTPs may not stop another affiliate.
Infection and Propagation Techniques
How attackers gain initial access to their target is highly varied due to the how different affiliates act “Since many affiliates distribute Lockbit, the access vectors they use are varied: from spear-phishing emails with malicious attachments to exploiting vulnerabilities in publicly facing applications and using stolen VPN and RDP credentials. The Lockbit affiliates are known to also buy access from other parties.” 6. The Cybersecurity & Infrastructure Security Agency (CISA) advisory on Lockbit 3.0 documents some of the common initial access techniques and maps them to the Mitre ATT&CK framework “Affiliates deploying Lockbit 3.0 ransomware gain initial access to victim networks via remote desktop protocol (RDP) exploitation [T1133], drive-by compromise [T1189], phishing campaigns [T1566], abuse of valid accounts [T1078], and exploitation of public-facing applications [T1190].” 7.
Once an affiliate has infiltrated a network, they deploy Lockbit and it begins to act as a tool to support lateral movement through various techniques that are implemented natively within the malware “Lockbit 3.0 attempts to spread across a victim network by using a preconfigured list of credentials hardcoded at compilation time or a compromised local account with elevated privileges [T1078]. When compiled, Lockbit 3.0 may also enable options for spreading via Group Policy Objects and PsExec using the Server Message Block (SMB) protocol. Lockbit 3.0 attempts to encrypt [T1486] data saved to any local or remote device, but skips files associated with core system functions.” 7. In addition to the “out of the box” functionality within the Lockbit malware affiliates have also been observed using various free and open-source tools to support network reconnaissance, remote access and tunnelling, credential dumping, and file exfiltration 1. If the affiliate can compromise other systems or gain credentials through their own TTPs they can then use them in conjunction with the Lockbit malware to gain deep penetration into the victim network maximizing lateral movement and persistence.
The combination of multiple affiliates being involved using various TTPs against targets across multiple industries makes Lockbit extremely hard to specifically defend against. The Federal Bureau of Investigation (FBI), CISA and Multi-State Information Sharing & Analysis centre (MS-ISAC) briefing #StopRansomware: Lockbit 3.0, 2023 provides an excellent summary of Indicators of Compromise (IoCs), TTPs and mitigation advice. Due to the variety of tools used across multiple affiliates mitigation techniques against initial access are generalized outlining standard practices in defending against most attackers. The report provides multiple IOCs and TTPs specific to the Lockbit malware itself which can be implemented to defeat installation and propagation of the malware if an attacker were to gain initial access.
Payload Information & Obfuscation Techniques
Lockbit 3.0 payload is comprised of three separate attack tools: 1. Lockbit ransomware: Used to compromise and encrypt Microsoft Windows end points and servers similar to other ransomware variants 2. Lockbit Linux-ESXi Locker: Targets the Linux operating system and the VMware ESXi hypervisor 3. StealBit: A custom data exfiltration tool used to upload data to dark web (ToR) sites.
As of Lockbit 2.0 the main components of Lockbit had evolved into a tool that is highly efficient at encrypting large amounts of data rapidly while simultaneously exfiltrating data to a custom storage location to maximise impact to targets before the ransomware is detected as well as exfiltrate data to a location that is safe from law enforcement being able to issues takedown orders as they would with commercial storage providers. The Lockbit developers appear to take pride in the quality of their work and are happy to boast about it on their dark web forums and in interviews. One of the Lockbit developers was interviewed in 2021 and published on a Russian open-source intelligence (OSINT) Youtube channel. When asked about the Lockbit 2.0 update this was his response:
“Q: The Lockbit 2.0 update has recently appeared. What are the most significant changes in a new version of the software?
A: We continue to move in our own direction. Lockbit, unlike other RaaS, is, first of all, a software complex and only then a set of related services. Our mission is to provide a tool that will help to carry out an attack as soon as possible. The most significant changes are the increase in encryption speed without losing quality and, of course, a stealer [StealBit – KELA] that automatically downloads all important data of a company to the administrative panel. Clients of the affiliate program [affiliates of the RaaS program – KELA] no longer need to mess with servers and cloud storage services, wasting time on the routine job and subsequently losing data after a first complaint filed to the cloud provider. In addition, now all the company’s data is stored in our TOR blog with the ability to download each file separately thanks to a listing [Lockbit’s blog posts now include a live file explorer through which one can see the exact files that were leaked and download each one separately – KELA]. There is no other affiliate program on the planet with such an arsenal.” 12. One of the tactics used to increase the speed at which Lockbit can encrypt a target’s data was to only encrypt the first 4KB of the data “Lockbit 2.0, for example, encrypts only the first 4KB of each file, which is enough to render them unreadable and unusable while also allowing the attack to complete very fast before incident responders have time to shut down systems and isolate them from the network.” 6. The extension “.lockbit” is then added to the encrypted file name a ransom note with the filename
.README.txt is copied to the device and the device’s wallpaper and icons are changed to Lockbit 3.0 branding.
Lockbit employs multiple Obfuscation techniques within their malware, communications channels, and associated tools. “Lockbit 3.0 will send encrypted host and bot information to its command and control (C2) servers [T1027]. Lockbit affiliates may perform software packing or virtual machine software protection to conceal their code. Blister Loader has been used for such purpose. [T1027.002].” 1. PowerShell, batch scripts and tools used for persistence are also obfuscated to avoid detection 6. In Lockbit 3.0 functionality was implemented to compile custom versions of their attack tools per affiliate and optionally encrypt the resulting binary so that a password is required to operate the custom-built attack package. “If a Lockbit affiliate does not have access to passwordless Lockbit 3.0 ransomware, then a password argument is mandatory during the execution of the ransomware. Lockbit 3.0 affiliates failing to enter the correct password will be unable to execute the ransomware [T1480.001]. The password is a cryptographic key which decodes the Lockbit 3.0 executable. By protecting the code in such a manner, Lockbit 3.0 hinders malware detection and analysis with the code being unexecutable and unreadable in its encrypted form. Signature-based detections may fail to detect the Lockbit 3.0 executable as the executable’s encrypted potion will vary based on the cryptographic key used for encryption while also generating a unique hash. When provided the correct password, Lockbit 3.0 will decrypt the main component, continue to decrypt or decompress its code, and execute the ransomware.” 7. The ability to encrypt the custom built version of Lockbit 3.0 for affiliates ensures that the deployed payload can only be controlled by the affiliate with the appropriate password and acts as an effective obfuscation tool. This custom compiled version of the ransomware combined with the encryption also serves to defeat signature-based defense technologies as it changes the signature of the payload.
Detection Techniques and Mitigation Actions
Given the vast variability in TTPs, IoCs and tools used by Lockbit affiliates to compromise victim networks it is difficult to describe any Lockbit specific techniques that can be used to detect attacks and initial compromise specific to the Lockbit ransomware. Mitigation techniques for attack and compromise are traditional mitigations that should be employed to defend against any attacker including but not limited to implementing a data recovery plan, adopting modern National Institute for Standards and Technology (NIST) recommendations for password polices documented in “NIST Special Publication 800-63-3 Digital Identity Guidelines” 8, require multi-factor authentication (MFA) and keep systems up to date with the last security patches. An extensive list of mitigation techniques that will protect against Lockbit and affiliates can be found in the MITIGATIONS section of the CISA cybersecurity advisory on Lockbit 7.
To protect against Lockbit infection and propagation, the same CISA cybersecurity advisory 7 is again a leading source of comprehensive up-to-date information. The advisory lists several IoCs that can be used to detect the malware within an environment which could be used to defeat infection or minimise impact if an affiliate attempts to deploy Lockbit for encryption and exfiltration. Some examples include:
Lockbit Command Line Parameters
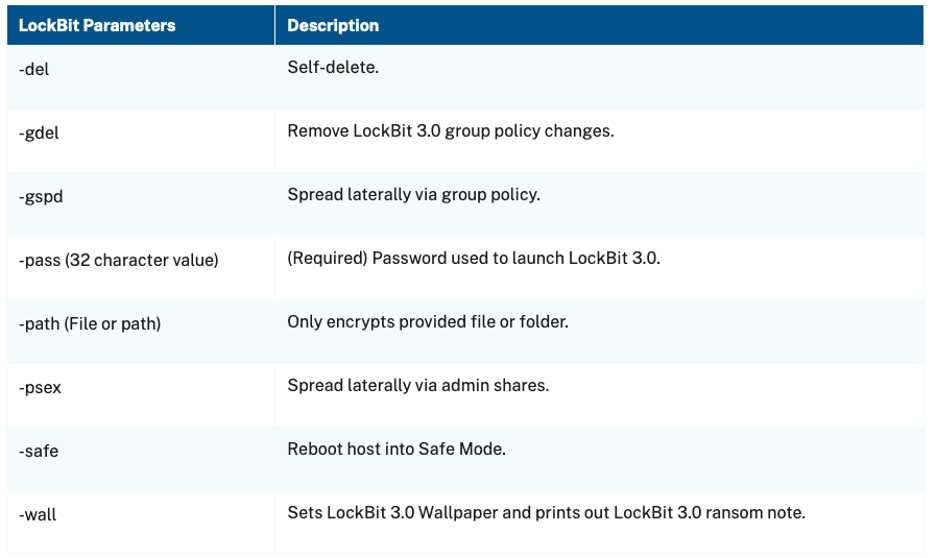
Figure 4: Lockbit command line parameters (#StopRansomware: Lockbit 3.0, 2023)
Mutual exclusion object (MUTEX) creation “When executed, Lockbit 3.0 will create the mutex, Global\
Registry Artifacts
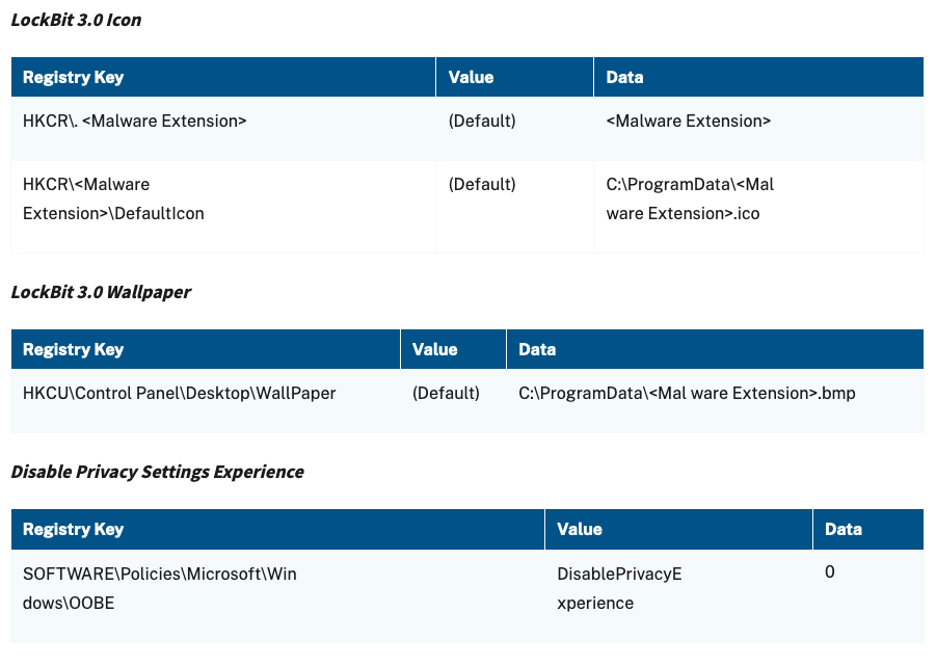 Figure 5 Lockbit 3.0 registry artifacts (#StopRansomware: Lockbit 3.0, 2023)
Figure 5 Lockbit 3.0 registry artifacts (#StopRansomware: Lockbit 3.0, 2023)
Group Policy Artifacts
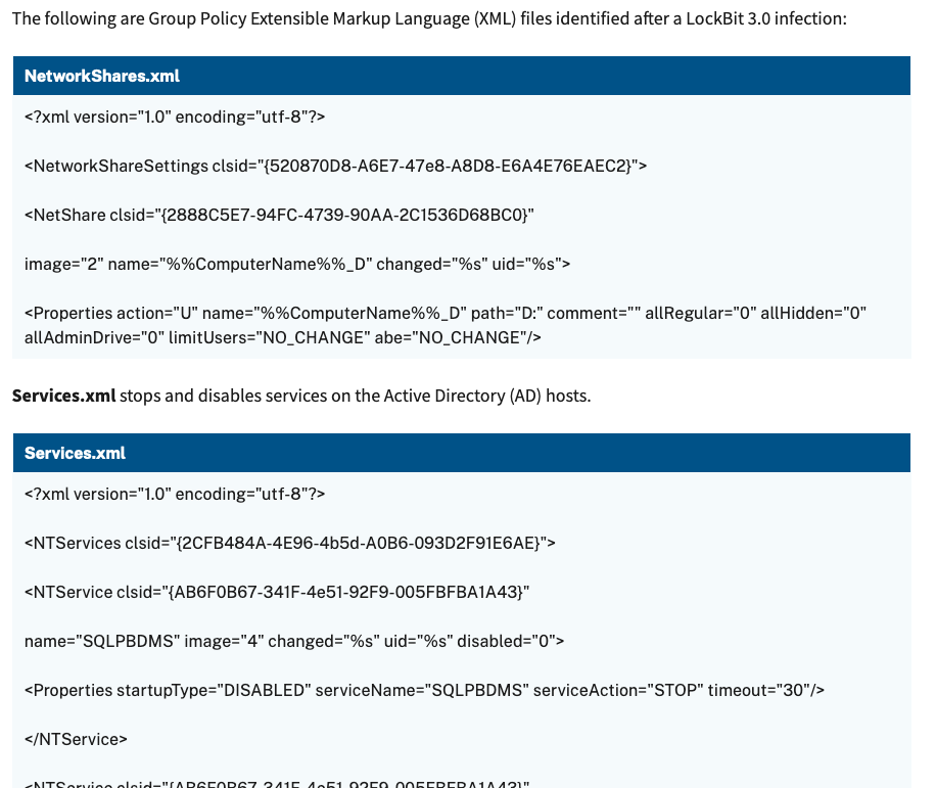
Figure 6 Lockbit 3.0 group policy artifacts (#StopRansomware: Lockbit 3.0, 2023)
Refer to the CISA advisory #StopRansomware: Lockbit 3.0, 2023 for the complete list of TTPs and IoCs that can be used with technical controls such as corporate Endpoint Detection and Response (EDR), Security Information and Event Management (SIEM) and Intrusion Prevention Systems (IPS) to detect and contain Lockbit.
Impacts of Lockbit
Targets and Effects
Since Lockbit functions as RaaS targets are inconsistent and span multiple industries because the targets are chosen by the affiliate. A quick snapshot from the group’s The Onion Router (ToR) dark web site demonstrates real-time the organisations that have recently been compromised by Lockbit affiliates.
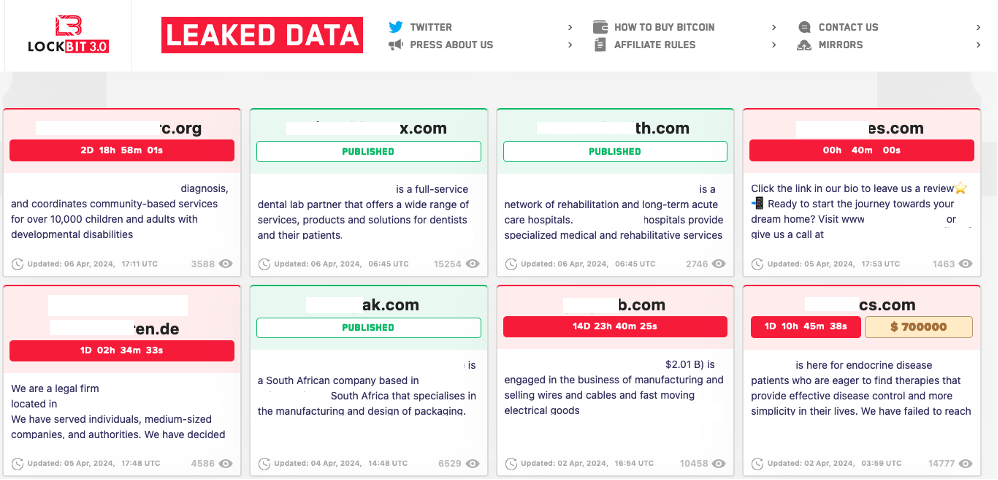 Figure 8 Screenshot of Lockbit dark web blog April 7, 2024
Figure 8 Screenshot of Lockbit dark web blog April 7, 2024
The Lockbit blog is part of the infrastructure supplied to affiliates, it acts as a platform to host exfiltrated data, set deadlines for payment and post exfiltrated data publicly should the extortion terms not be met by the deadline. When compromised targets fail to pay the sensitive information that was exfiltrated as part of the attack is published openly on their TOR dark web blog for anyone to download and use as they will.
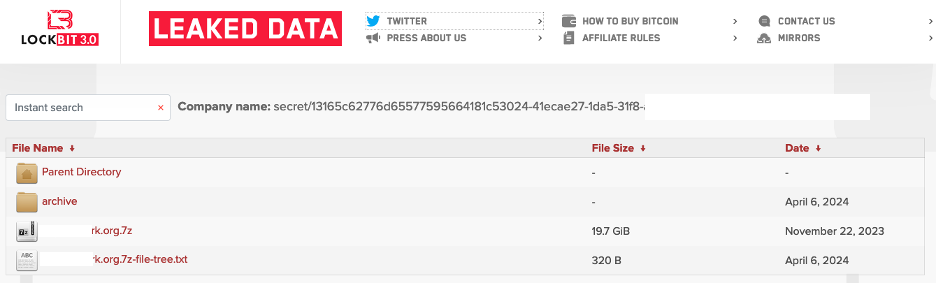 Figure 9 Recently leaked data on Lockbit TOR dark web blog
Figure 9 Recently leaked data on Lockbit TOR dark web blog
Although Lockbit does have rules for affiliates that claim to prohibit attacks on organisations that could “lead to death” these rules are extremely vague and given how their RaaS functions it would be difficult for the Lockbit operators to enforce. Reading through the affiliate rules really does give one a snapshot into the mind of the Lockbit operators and their lack of empathy for their victims.
 Figure 10 screen shot of Lockbit Affiliate rules
Figure 10 screen shot of Lockbit Affiliate rules
Their rules state that “It is forbidden to encrypt institutions where damage to the files could lead to death, such as cardiology centers, neurosurgical departments, maternity hospitals and the like, that is, those institutions where surgical procedures on high-tech equipment using computers may be performed.”. However, they go on to state that attacks on these types of institutions are still allowed “It is allowed to steal data from any medical facilities without encryption, as it may be a medical secret and must be strictly protected in accordance with the law.”.
Costs and Losses
The explosion of ransomware attacks has had a significant financial impact on compromised organisations that have paid the extortion fees. Given the rise of Lockbit as one of the most successful RaaS operators they have caused financial damages into hundreds of millions of dollars “Lockbit members have executed attacks against thousands of victims in the United States and around the world, according to the U.S. Department of Justice (DOJ). First surfacing in September 2019, the gang is estimated to have made hundreds of millions of U.S. dollars in ransom demands and extorted over $120 million in ransom payments.” 2. However, the ransom payments only tell part of the financial story the costs to businesses revenue due to reputational damage and costs to recover from a Lockbit infection cannot be measured but would far exceed the hundreds of millions that have been paid in ransom.
More alarming than the financial losses caused by Lockbit and their affiliates is the impact to human life. The Lockbit operators appear to do little to discourage attacks on organisations that would be against their affiliate rules. Reaction after a prohibited organisation has had significant interruptions to business operations is too late from the perspective of a target organisation that has already been impacted. Although the terms clearly state that organisations providing healthcare where disruption to services could lead to loss of life the Hospital For Sick Children (SickKids Hospital) in Toronto Ontario suffered an attack resulting in significant impact to patient care services as result in January of 2023. Once the story made international press Lockbit operators did respond, issue an apology, and release the decryption keys 9. However the damage had been done, the hospital that cares for critically ill children was cast into a state of emergency that lasted weeks or months “A ransomware attack has delayed lab and imaging results at Toronto’s Hospital for Sick Children and could lead to longer wait times, the hospital said Thursday, noting that some of its systems could be offline for weeks.” 10.
If Lockbit continues to be able to operate with impunity the financial impacts and more importantly impact to human life will continue. As of the writing of this paper Lockbit is one of many RaaS groups in operation, often with nation state support and the problem continues to be one of the largest challenges for law enforcement and IT security experts across the planet.
Outlawing Ransomware Payments
This is a hotly debated topic. As the UK continues the conversation on reducing or banning ransomware payments through legislation this topic warrants an ongoing conversation.
I have been on both sides of the fence of this discussion. While I do agree with the premise that the decision to pay should be up to the organisation and building capability to recover should be a priority 11 I'm really leaning towards the side of outlawing payments, at least in some situations. As we can see with Lockbit the operators of RaaS are highly functional organised crime rings. It's not unreasonable for it to be illegal to make payments to traditional organised crime so why should it be when it comes to digital crime? Paying the ransom is not a quick way to recovery as we witnessed with the Change Healthcare Incident. If an organisation does pay you still have to deal with full incident forensics and service restoration. Yes restoration could be expedited by unlocking key systems in an isolated environment but organisations are much better served investing in immutable backups with quick recovery capabilities ahead of time. The only situation that payment can be useful is when those backups do not exist which should be fairly minimal today.
My current thoughts on the topic is that it does make sense for publicly funded organistions to outlaw payment coupled with strong messaging from governments. Publicly funded organisations often don't have the financial resources to invest in mature cybersecurity programs and have been a constant target as a result of that. Healthcare systems, municipalities and small law enforcement branches are easy pickings for advanced organised crime groups like Lockbit. Making payment illegal and publicly announcing it would eliminate the financial motivation and detour attackers. I have heard the counter argument "Publicly announcing you won't pay paints a target on your back.". From my perspective crossing your fingers and living in fear of taking a strong stance is a much more risky stance to take. Outlawing payment by public sector organisations, sending a strong message about that and not backing down would elminate the financial incentive which is the #1 motivator for organised criminal groups.
References
-
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-165a ↩↩↩
-
https://krebsonsecurity.com/2024/02/feds-seize-lockbit-ransomware-websites-offer-decryption-tools-troll-affiliates/ ↩↩↩
-
https://www.bleepingcomputer.com/news/security/lockbit-ransomware-returns-to-attacks-with-new-encryptors-servers/ ↩
-
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-165a ↩
-
https://www.csoonline.com/article/573095/lockbit-explained-how-it-has-become-the-most-popular-ransomware.html ↩↩↩
-
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-075a ↩↩↩↩↩
-
https://globalnews.ca/news/9367174/ransomware-attack-sickkids-toronto/ ↩
-
https://www.healthcareinfosecurity.com/uk-lawmakers-dont-hear-fervor-for-ransomware-payment-ban-a-27636 ↩
-
https://www.kelacyber.com/lockbit-2-0-interview-with-russian-osint/ ↩